 I’ve spoken about password managers (and using good passwords) before…maybe once or twice…or a lot… One of the huge benefits of a password manager is that you can use excellent and strong and unique passwords but you don’t have to remember them; the password manager does it all for you. The way the password manager works is by storing your super strong password and then pasting it into the password box on the website for you. For whatever reason, some web developers have decided to not let you paste these ultra strong passwords into the password box on the website.
I’ve spoken about password managers (and using good passwords) before…maybe once or twice…or a lot… One of the huge benefits of a password manager is that you can use excellent and strong and unique passwords but you don’t have to remember them; the password manager does it all for you. The way the password manager works is by storing your super strong password and then pasting it into the password box on the website for you. For whatever reason, some web developers have decided to not let you paste these ultra strong passwords into the password box on the website.
I. HATE. THIS!!!
What in the hell is this supposed to accomplish besides pissing people off?!? Yes, I know there’s an argument on the other side but I’m going to give it zero airtime because the argument is two decades old and not at all in keeping with modern security practices.
Luckily, there’s a fix.
What Are You Waiting For? Tell Me The Fix!
There are two different ways to accomplish this. The easy way is through an add-on/extension for your web browser.
- For Chrome: Jacob Swanner‘s excellently-named extension Don’t Fuck With Paste
- For Firefox: Aaron Raimist’s also excellently-named copycat extension Don’t Fuck With Paste
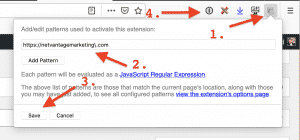 Simply install & activate the extension, then:
Simply install & activate the extension, then:
- Click the extension icon
- Add the appropriate URL (auto-populated to the current website)
- Click the “save” button
- Also notice that I use a password manager and you should too!
After activating the extension and saving the correct domain you will be able to paste into any restricted password field on the website.
To undo the paste-blocking, click the extension icon (1.), remove the website in question (via the “x” to the right of the website name), and click “save” (3.).
The (Slightly) More Difficult Way
I don’t know about you but I try to avoid adding extra extensions, add-ons, plugins, etc. to just about everything. I avoid this if at all possible because every extra bit of software you run adds a little bit of heft and bloat and makes things a little slower; adds one more way for things to go wrong; adds one more attack vector for the Böse Herren to infiltrate your system(s).
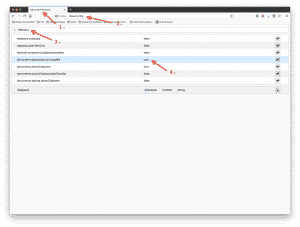 In Firefox (sorry Chrome users) you can edit the configuration files to disallow paste-blocking. To do this…
In Firefox (sorry Chrome users) you can edit the configuration files to disallow paste-blocking. To do this…
- Open a new tab
- Type about:config into the address bar
- Type clipboard into the search box
- Double-click the entry that says dom.event.clipboardevents.enabled so that the value changes from “true” to “false.”
- Close that browser tab
Viola! Paste-blocking enabled!
To undo this kind of paste-blocking simply repeat all of the above steps and ensure that, at step 4., the value is set to “true.”
Bonus Method
There’s a third method I discovered while researching this blog post. Every major browser has some form of Developer Tools that will allow advanced users to tinker with the website code while it’s in the browser. This third method instructs you to open the Developer Tools and remove the javascript controlling the paste-blocker. I’ve never used this method but it makes logical sense and I see no reason why it wouldn’t work. One caveat, however, is that this method is temporary–you have to remove that JS every time you reload the page with the password field. The previous two methods are more permanent in that they will block the JS forever until you disable them.
The One Downside I’ve Found
Unfortunately, I’ve found that both methods #1 and #2 can cause some undesirable behavior. I’ve noticed that, while you’ve got paste-blocking disabled sometimes…and this is ironic A.F….you cannot paste text into text fields in certain web applications. I noticed this most while using method #2 on the Firefox browser in WordPress. I would go to paste something into my blog post (in visual editing mode) and it refused to paste. I could get it to paste using the non-visual (i.e. text) writing method…which was double odd. Regardless, it caused problems when authoring web content.
For whatever reason, using the paste-blocking plugins has the same weird side effect. The advantage with the plugin, however, is that enable/disable it on a per-domain basis so it only affects those specific domains for which you have set it up. Method #2 is more of a “carpet bomb” option where you enable the feature for the entire browser.
Therefore, I would recommend using the plugin method instead of the configuration file method. At least this way you are affecting paste-blocking only on specific domains instead of within the entire browser. I suppose Method #3. (removing the JS using Developer Tools) is a good option as well. Truth be told, I’ve only encountered paste-blocking on signup pages when registering for an account on a new website. Using that as a yardstick, I suppose Method #3. would be best…but, again, I’ve never tried it.
Anyone Have A Better Way?
I’m always on the lookout for a better way to work and a more logical way to do things. If you’ve got some technique that you use or like, holler and let me know!

Here’s a gem: cannot paste from a pw manager into the AppleID pw required to upgrade iOS. (et. al. browser workarounds do not apply)
Yeah…Apple has their stuff locked down pretty hard. I’m also a fan of 1Password (password manager) and I use Apple products almost exclusively. There are lots of nice things about that ecosystem but the method in which iCloud handles passwords and password updates frustrates me to no end. I wish there were an easy work-around but I have yet to find one.